SSL Handshake Message Sequence
What is the SSL handshake message sequence? I want to know how many messages are exchanged between the client and the server.
✍: FYIcenter
![]() When a SSL client is connecting to a SSL server, they will communicate
to each other with the following sequence of messages to perform SSL handshake
and exchange application data securely encrypted:
When a SSL client is connecting to a SSL server, they will communicate
to each other with the following sequence of messages to perform SSL handshake
and exchange application data securely encrypted:
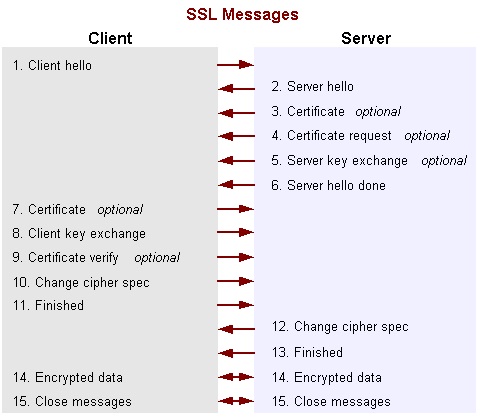
- Client hello - The client sends the server information including the highest version of SSL that it supports and a list of the cipher suites that it supports (TLS 1.0 is indicated as SSL 3.1). The cipher suite information includes cryptographic algorithms and key sizes.
- Server hello - The server chooses the highest version of SSL and the best cipher suite that both the client and server support and sends this information to the client.
- Certificate (optional) The server sends the client a certificate or a certificate chain. A certificate chain typically begins with the server's public key certificate and ends with the certificate authority's root certificate. This message is optional, but is used whenever server authentication is required.
- Certificate request (optional) If the server must authenticate the client, then it sends the client a certificate request. In Internet applications, this message is rarely sent.
- Server key exchange (optional) The server sends the client a server key exchange message if the public key information from the certificate is not sufficient for key exchange. For example, in cipher suites based on Diffie-Hellman (DH), this message contains the server's DH public key.
- Server hello done The server tells the client that it is finished with its initial negotiation messages.
- Certificate (optional) If the server requested a certificate from the client, the client sends its certificate chain, just as the server did previously.
- Client key exchange The client generates information used to create a key to use for symmetric encryption. For RSA, the client then encrypts this key information with the server's public key and sends it to the server. For cipher suites based on DH, this message contains the client's DH public key.
- Certificate verify (optional) This message is sent by the client when the client presents a certificate as previously explained. Its purpose is to allow the server to complete the process of authenticating the client. When this message is used, the client sends information that it digitally signs using a cryptographic hash function. When the server decrypts this information with the client's public key, the server is able to authenticate the client.
- Change cipher spec The client sends a message telling the server to change to encrypted mode.
- Finished The client tells the server that it is ready for secure data communication to begin.
- Change cipher spec The server sends a message telling the client to change to encrypted mode.
- Finished The server tells the client that it is ready for secure data communication to begin. This is the end of the SSL handshake.
- Encrypted data The client and the server communicate using the symmetric encryption algorithm and the cryptographic hash function negotiated during the client hello and server hello, and using the secret key that the client sent to the server during the client key exchange. The handshake can be renegotiated at this time. See the next section for details.
- Close Messages At the end of the connection, each side sends a close_notify message to inform the peer that the connection is closed.
Diagram below shows the sequence of messages that are exchanged in the SSL handshake:
⇒ SSL Handshake Message Examples
⇐ -Djavax.net.debug - jsse.jar Debugging Options
2018-03-24, 1281🔥, 0💬